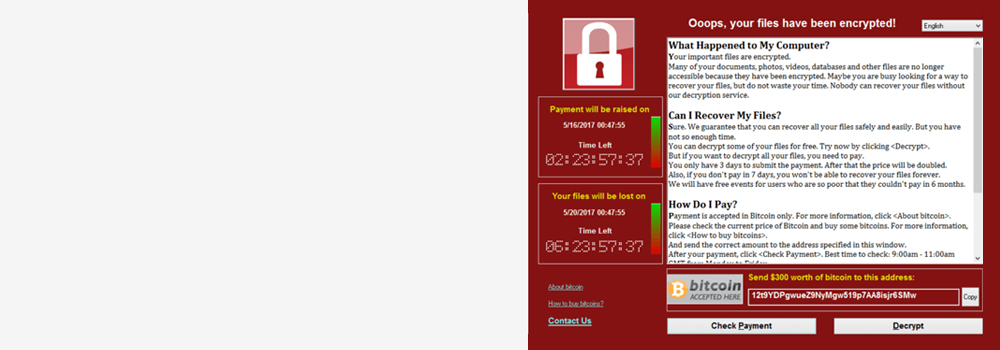
Ransomware Data Recovery Services – Oxford Data Recovery
At Oxford Data Recovery, we specialise in ransomware data recovery for all types of systems, including business, company, and personal computers. With over 10 years of Ransomware experience, we have successfully recovered data from ransomware-encrypted systems, including RAID servers, desktop computers, small servers, and laptops. Our forensic lab employs advanced techniques to decrypt data and restore functionality.
Our Expertise in Ransomware Data Recovery
- RAID Servers:
- Recovery from encrypted RAID arrays used in businesses and enterprises, including Dell and HP servers
- Desktop Computers and Laptops:
- Decrypting personal and business systems affected by ransomware.
- Small Servers:
- Data recovery for small businesses and SOHO setups.
Advanced Forensic Techniques
- Cryptographic Analysis:
- Examining encryption patterns and ransomware-specific key structures.
- Key Extraction:
- Recovering keys where possible from residual data or attacker misconfigurations.
- Virtual Machine Sandbox Testing:
- Running ransomware simulations in secure environments to study its behaviour.
- Sector-Level Data Recovery:
- Restoring data from raw disk images, bypassing encryption layers when feasible.
- Collaborations with Global Experts:
- Leveraging industry partnerships to identify decryption tools and solutions.
Evolution of Ransomware (2015–2024)
The evolution of ransomware over the last decade has seen increasingly sophisticated methods targeting various sectors. Below are some of the most impactful variants and trends during this period:
1. 2015–2017: The Early Widespread Threat
- CryptoLocker: One of the first major ransomware families to gain global notoriety.
- TeslaCrypt: Targeted gamers by encrypting game files and progress.
- Locky: Spread via email attachments, encrypting various document formats.
- Cerber: Known for advanced evasion techniques and targeting cloud services.
2. 2018–2020: Enterprise-Targeted Ransomware
- SamSam: Targeted healthcare and government sectors, demanding high ransoms.
- Ryuk: Known for targeting enterprises and demanding multi-million-dollar ransoms.
- Dharma: Spread via remote desktop protocol (RDP) exploits, focusing on SMBs.
- Maze: Combined encryption with data theft, threatening public leaks.
3. 2021–2024: Ransomware-as-a-Service (RaaS)
- REvil (Sodinokibi): Infamous for high-profile attacks on global corporations.
- Conti: A RaaS operation that focused on double extortion tactics.
- DarkSide: Responsible for the Colonial Pipeline attack, causing widespread disruption.
- Clop: Targeted financial institutions and used extortion websites.
- LockBit: Focused on fast encryption and operational resilience, affecting large-scale enterprises.
Industries Affected by Ransomware
- Healthcare:
- Hospitals and clinics targeted for sensitive patient data.
- Education:
- Universities and schools compromised for personal student records.
- Government:
- Municipalities and state organizations affected, crippling public services.
- Finance:
- Banks and financial institutions targeted for high-value data.
- Small and Medium Businesses:
- Often targeted due to weaker cybersecurity defenses.
Common Signs of Ransomware Attacks
- Sudden inability to access files with extensions like .locked, .crypt, or .enc.
- Display of a ransom note demanding payment in cryptocurrencies.
- Slow system performance due to encryption processes running in the background.
- Encrypted filenames or changes to file extensions.
Our Ransomware Recovery Process
1. Assessment and Diagnosis
- Identify the ransomware variant and encryption type.
- Evaluate the extent of data loss and potential recovery options.
2. Containment
- Isolate infected systems to prevent further spread.
- Provide immediate guidance to secure backups and prevent additional damage.
3. Decryption and Recovery
- Utilise decryption tools for known ransomware families.
- Implement advanced forensic techniques to bypass encryption or recover keys.
4. Data Restoration
- Recover and restore data from encrypted volumes or backup systems.
- Validate data integrity and ensure operational continuity.
5. Post-Recovery Support
- Provide guidance on improving cybersecurity to prevent future attacks.
- Offer ransomware-specific solutions like endpoint detection and response (EDR).
Why Choose Oxford Data Recovery?
- 10+ Years of Ransomware Recovery Experience:
- Expertise across all major ransomware families and attack vectors.
- Advanced Forensic Tools:
- Cutting-edge technology for analysing and mitigating ransomware threats.
- High Success Rates:
- Proven track record of recovering data from complex ransomware attacks.
- Confidential and Secure:
- Strict adherence to data privacy and security protocols.
- 24/7 Emergency Services:
- Immediate response to ransomware incidents.
Tips to Mitigate Ransomware Risk
- Backup Regularly:
- Maintain both online and offline backups.
- Patch Systems:
- Regularly update operating systems and software.
- Train Employees:
- Educate staff on phishing and ransomware prevention.
- Implement Endpoint Security:
- Use antivirus and anti-ransomware solutions.
- Limit Privileges:
- Restrict admin rights to reduce exposure.
Contact Us Today
For reliable and professional ransomware data recovery services, trust Oxford Data Recovery. Schedule your free consultation now, and let us help you recover your valuable data from ransomware-encrypted systems!